What is a Firewall?
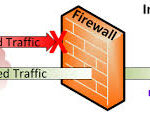
A firewall is a security device or software program designed to control the flow of network traffic between two or more computer networks. It acts as a barrier between a trusted, secure internal network and an untrusted external network, such as the Internet, to prevent unauthorized access and protect against cyber threats.
Firewalls use a set of rules to filter incoming and outgoing traffic based on predetermined criteria, such as the type of network service or application being used, the source and destination IP addresses, and the port numbers. By examining network packets, firewalls can block or allow traffic based on these rules to ensure that only authorized traffic is allowed through.
Firewalls can be implemented as hardware devices, software programs, or a combination of both, and are commonly used in enterprise networks, small businesses, and home networks to provide an additional layer of security against cyber attacks.
Types of Firewalls
Packet filtering firewall:
This type of firewall filters incoming and outgoing network traffic based on predetermined rules, such as source and destination IP addresses, port numbers, and protocols. Packet filtering firewalls are simple and fast, but they offer limited protection against more sophisticated cyber threats.
Stateful firewall:
This type of firewall monitors the state of network connections and only allows traffic that belongs to an established connection or a related connection. Stateful firewalls provide better protection against certain types of cyber attacks, such as port scanning and denial-of-service (DoS) attacks.
Proxy firewall:
This type of firewall intercepts network traffic and acts as an intermediary between the client and the server, filtering traffic based on application-level data. Proxy firewalls provide more advanced security features, such as content filtering and application-level security, but they can also be slower and more complex to configure.
Next-generation firewall:
This type of firewall combines the features of traditional firewalls with advanced security technologies, such as intrusion prevention systems (IPS), deep packet inspection (DPI), and application awareness. Next-generation firewalls are designed to provide more comprehensive protection against a wide range of cyber threats, but they can also be more expensive and complex to manage.
Cloud firewall:
This type of firewall is hosted in the cloud and can be deployed to protect cloud-based applications and services. Cloud firewalls offer scalability, flexibility, and ease of management, but they may also introduce additional latency and dependencies on third-party providers.
Each type of firewall has its own advantages and disadvantages, and choosing the right type depends on factors such as the organization’s security requirements, budget, and network architecture.
How Does a Firewall Work?
A firewall works by examining incoming and outgoing network traffic and filtering it based on a set of predefined rules. The basic function of a firewall is to determine whether a particular packet or stream of data should be allowed to pass through the firewall or not.
Here are the steps involved in how a firewall works:
Traffic inspection:
The firewall inspects network traffic to determine whether it meets the criteria specified in the firewall rules. This inspection can be done at the packet level (packet filtering) or at the application level (proxy filtering).
Packet filtering:
In packet filtering, the firewall examines the packet headers to determine the source and destination addresses, port numbers, and other characteristics. The firewall then compares this information to its set of rules to determine whether the packet should be allowed to pass through the firewall.
Proxy filtering:
In proxy filtering, the firewalls acts as an intermediary between the client and the server. The firewalls intercepts traffic and examines the contents of the packet to determine the application-level data. The firewalls then compares this information to its set of rules to determine whether the traffic should be allowed to pass through the firewall.
Policy enforcement:
If the traffic meets the criteria specified in the firewalls rules, the firewalls allows it to pass through to its destination. If the traffic does not meet the criteria, the firewalls blocks it or sends an alert to the administrator.
Logging and reporting:
The firewalls logs all traffic that passes through it, including allowed and blocked traffic. This information can be used to troubleshoot network issues, monitor network usage, and detect potential security threats.
They are a critical component of network security and are commonly used in enterprise networks, small businesses, and home networks to protect against cyber threats.
Read also : – Diet and Nutrition: Onions Have Many Health Benefits
Could Healthy Eating at any Point Assist You With Getting Fit?
Conclusion
In conclusion, a firewalls is a security device or software program designed to control the flow of network traffic between two or more computer networks. It acts as a barrier between a trusted, secure internal network and an untrusted external network, such as the Internet, to prevent unauthorized access and protect against cyber threats.
There are several types of firewalls, each with its own strengths and weaknesses, including packet filtering firewalls, stateful firewalls, proxy firewalls, next-generation firewalls, and cloud firewalls.
A firewalls works by examining incoming and outgoing network traffic and filtering it based on a set of predefined rules. The firewalls inspects network traffic to determine whether it meets the criteria specified in the firewalls rules and allows or blocks traffic accordingly. Firewalls are a critical component of network security and are commonly used to protect against cyber threats in enterprise networks, small businesses, and home networks.